How to Decode JWTs and Verify Signature
- Details
- Written by Nam Ha Minh
- Last Updated on 04 October 2024 | Print Email
In this post, I’ll share some easy ways to decode JSON Web Tokens (JWTs) into human-readable form so you can easily read the token’s content. It would be helpful in REST API development, as sometimes you need to check details of JWTs during API security testing, such as testing token generation, access token issuance, etc.
You’ll also learn how to verify the integrity of a JWT by verifying its signature, which is signed either by a secret key or a pair of public and private keys.
NOTES: this article is about how to decode unencrypted JSON Web Tokens. To verify signature, you must have the secret key or the public/private keypair.
1. Decode a JWT using a Base64 Decoder
You know, a JWT contains three parts: the header, the payload and the signature. The header and payload are encoded in Base64 format, so you can use any Base64 decoder to read their content.
You can simply google for “base64 decoder” and choose the first result, such as this Base64 Encode and Decode tool. Copy and paste the content of an access token you want to decode into the text area, then click on the “Decode” button, as shown in the following screenshot:
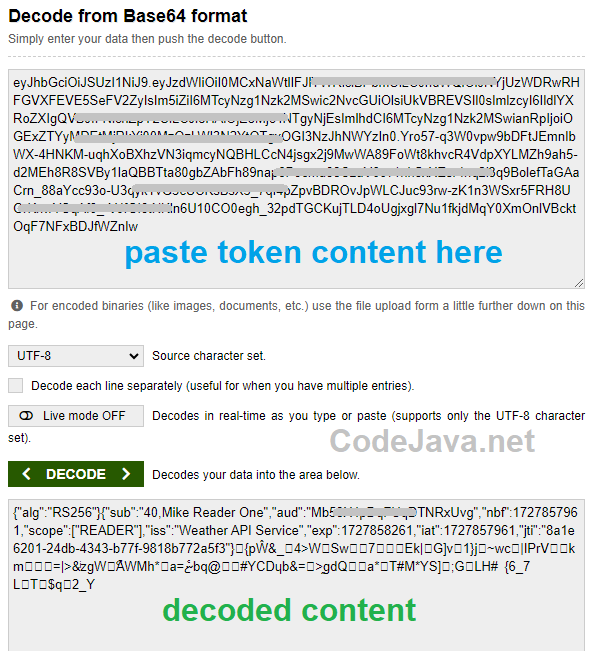
You’ll see the decoded content in the text area below. It shows the content of the header (algorithm) and the payload (claims). Notice that the last part is unreadable - this is the token signature. You’ll learn how to verify the JWT signature shortly.
2. Decode a JWT using a Dedicated JWT Decoder
For better decoding results, it’s recommended to use a dedicated JWT decoder such as JWT IO. It’s a neat tool that I prefer to use for checking my JWTs. Paste the content a JWT into the Encoded text area, and you’ll see it decoded immediately, as shown in the following screenshot (for example):
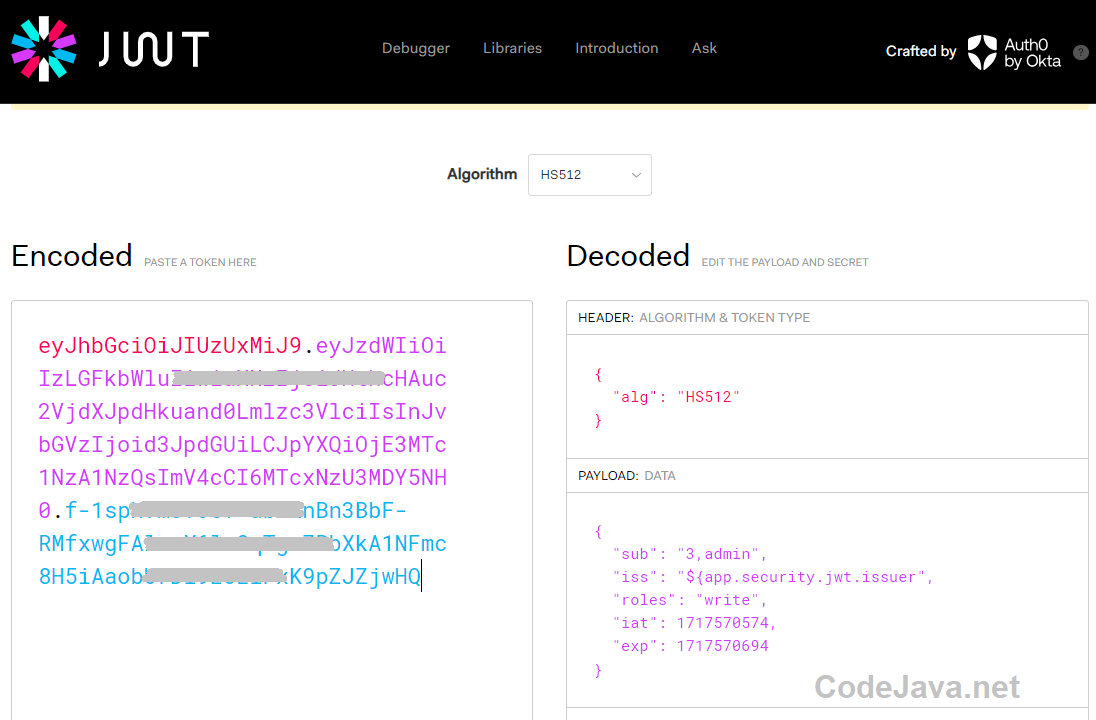
With this dedicated JWT decoder, the decoded information is presented in a clear and organized way: you can easily see the algorithm name, and the payload data is prettified in JSON format. That’s why I love this tool.
NOTES: In reverse, you can even modify content of the token (header and payload) and see the encoded result immediately. Try it out!
You can notice that it shows a warning in red, saying “Invalid Signature”:

Read the next paragraph to see how to verify the signature of the token.
3. Verify Signature Signed with Secret Key
The best part of the JWT IO’s decoder tool is that it allows you to check the integrity of JWTs by verifying the signature. If a JWT is signed with a secret key, it will prompt you to enter “your-256-bit-secret” under the Verify Signature section:
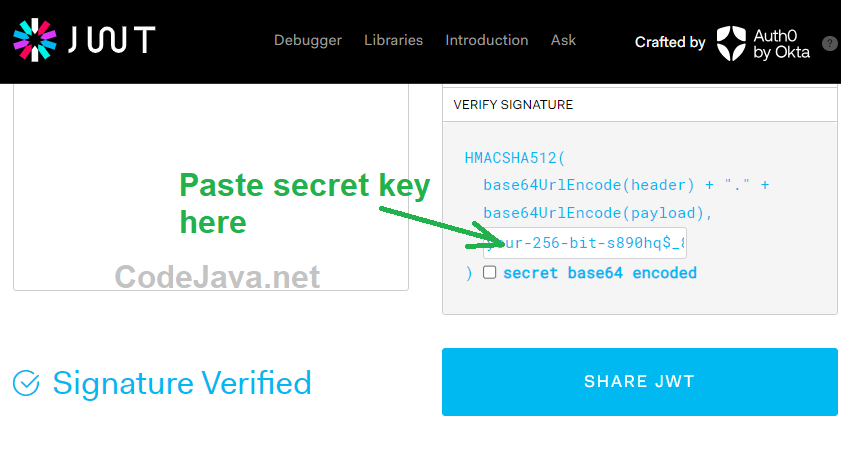
Paste the secret key into this text field, and you’ll see whether the token remains intact. If the token is original, it will display “Signature Verified” as shown in the above screenshot.
You can watch the following video to see how I use a public and private key pair to verify the signature of a JWT:
4. Verify Signature Signed with Public and Private Keys
A JWT can be signed using a public and private key pair. In that case, paste the content of the public key and the private key as shown below:
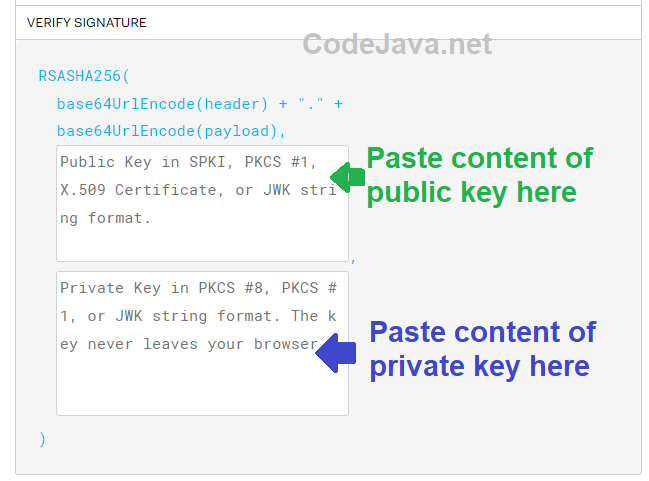
You may need to copy content from your public.pemand private.pem files. Note that you must copy the entire text, including the header line “-----BEGIN PRIVATE KEY-----“ or “-----BEGIN PUBLIC KEY-----“, and the footer line “-----END PRIVATE KEY-----” or “-----END PUBLIC KEY-----”.
Summary
So far, you have learned how to decode JSON Web Tokens (JWTs) using an online tool like JWT IO, allowing you to easily read the token’s content (header and payload). For token signature verification, you have also learned how to verify a JWT signature with a secret key or a public/private key pair. Hope you find this post helpful in enriching your REST API development experience.
Other REST API Tutorials:
- Java RESTful Web Services Tutorial for Beginner with Jersey and Tomcat
- Java CRUD RESTful Web Services Examples with Jersey and Tomcat
- Spring Boot Hello World RESTful Web Services Tutorial
- Spring Boot RESTful CRUD API Examples with MySQL database
- Spring Boot File Download and Upload REST API Examples
- Spring Boot REST API CRUD with HATEOAS Tutorial
- How to Use curl for Testing REST APIs (Test CRUD Operations)
- How to Use Postman for Testing REST APIs (Test CRUD Operations)
About the Author:
 Nam Ha Minh is certified Java programmer (SCJP and SCWCD). He began programming with Java back in the days of Java 1.4 and has been passionate about it ever since. You can connect with him on Facebook and watch his Java videos on YouTube.
Nam Ha Minh is certified Java programmer (SCJP and SCWCD). He began programming with Java back in the days of Java 1.4 and has been passionate about it ever since. You can connect with him on Facebook and watch his Java videos on YouTube.